Description:
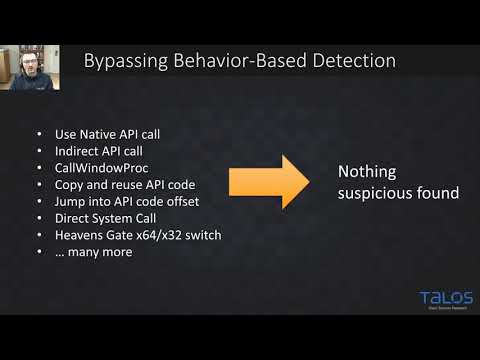
Analyze recent evolutions in malware loaders in this 54-minute conference talk from the Hack In The Box Security Conference. Explore the significant increase in malware loader volume and variety over the past year, examining how adversaries are shifting from malvertising to creating new botnets for distributing various malware payloads. Delve into the characteristics of this new generation of malware loaders, including increased obfuscation, modularization, and flexibility. Learn about techniques for hunting these loaders in corporate environments and methods for more effective analysis. Gain insights from Cisco Talos threat researchers as they discuss the changing landscape of malware distribution, multi-stage delivery tactics, and evasion techniques employed by cybercriminals.
Analyzing Recent Evolutions in Malware Loaders
Add to list
#Conference Talks
#Hack In The Box Security Conference
#Information Security (InfoSec)
#Cybersecurity
#Reverse Engineering
#Malware Detection
#Obfuscation