Description:
Explore the vulnerabilities in MediaTek's audio DSP firmware and Android API in this HITB Security Conference talk. Dive into the reverse engineering process of the custom Tensilica Xtensa microprocessor architecture used in MediaTek SoCs. Learn about the discovered security issues that could lead to local privilege escalation, eavesdropping on user conversations, and malicious code concealment. Gain insights into the unique challenges posed by MediaTek's custom instruction set and the research methodology employed to uncover these vulnerabilities. Understand the implications for the security of smartphones and IoT devices using MediaTek chips, which are present in approximately 37% of such devices worldwide.
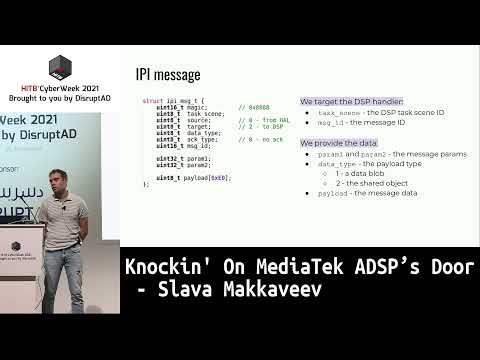
Knockin' On MediaTek ADSP's Door
Add to list
#Conference Talks
#Hack In The Box Security Conference
#Information Security (InfoSec)
#Reverse Engineering
#Engineering
#Electrical Engineering
#Embedded Systems
#Embedded Systems Security
#Firmware Security