Description:
Explore modern post-exploitation techniques in cloud environments through this 56-minute conference talk from Hack In The Box Security Conference. Delve into the attacker's mindset, focusing on exploiting weaknesses in Identity and Access Management (IAM) mechanisms within enterprise applications. Learn how attackers leverage compromised accounts in cloud-native organizations that lack traditional internal networks. Examine real-world scenarios using reproduced environments, covering topics such as modern enterprise architectures, app analysis for targeting, and a taxonomy of IAM-based methods for discovery, persistence, privilege escalation, and exfiltration. Gain insights into emerging security tools like CIEM, SSPM, and SMP, and understand evasion techniques. Benefit from the expertise of cybersecurity researcher Gal Diskin as he shares his extensive experience in the field.
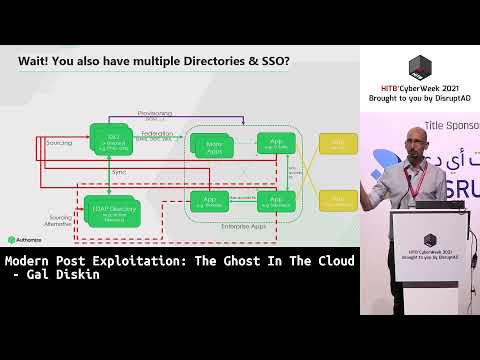
Modern Post Exploitation - The Ghost In The Cloud
Add to list
#Conference Talks
#Hack In The Box Security Conference
#Information Security (InfoSec)
#Cybersecurity
#Computer Science
#Information Technology
#Identity and Access Management (IAM)
#Enterprise Architecture
#Privilege Escalation