Description:
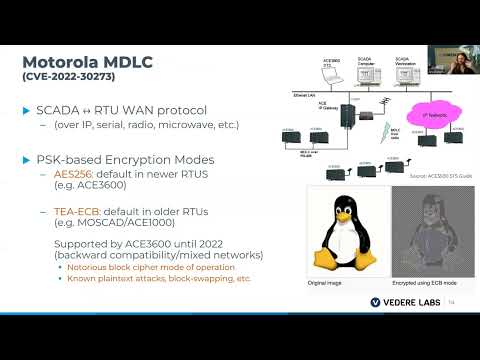
Explore the persistent challenges of insecure-by-design practices in Operational Technology (OT) devices and protocols in this comprehensive conference talk from the Hack In The Box Security Conference. Delve into dozens of previously undisclosed issues affecting products from nearly 20 vendors across various industrial sectors. Gain insights into the quantitative overview of these vulnerabilities, ranging from security-certified products with inherent design flaws to unsuccessful attempts at improvement. Examine how the opacity and proprietary nature of OT systems, coupled with suboptimal vulnerability management and potentially misleading security certifications, complicate risk management efforts. Through technical deep-dives, understand how attackers can achieve remote code execution on critical Level 1 devices using only intended functionality, and consider the defensive implications. Analyze quantitative data on the research process, providing valuable information on the resources required to develop basic offensive capabilities and their potential impact on the threat landscape.
Read more
ICEFALL - Revisiting A Decade Of OT Insecure-By-Design Practices
Add to list
#Conference Talks
#Hack In The Box Security Conference
#Information Security (InfoSec)
#Reverse Engineering
#Cybersecurity
#Remote Code Execution
#Engineering
#Electrical Engineering
#Embedded Systems
#Embedded Systems Security