Description:
Explore the intricacies of compiler security testing in this conference talk from the Hack In The Box Security Conference. Delve into the challenges of testing compiler components like optimizers and code generators, which can introduce security vulnerabilities in smart contracts. Learn about structured approaches to overcome limitations of traditional fuzzing techniques when dealing with complex programming languages like Solidity. Discover innovative methods for generating valid test programs, implementing differential testing, and employing execution tracing to uncover bugs in compiler optimizations and code generation. Examine real-world examples of security-relevant bugs found in the Solidity compiler, including incorrect keccak computations and faulty optimizations. Gain insights into the effectiveness of combining heuristics with randomness in compiler testing, and understand the impact and severity of discovered vulnerabilities across different compiler components.
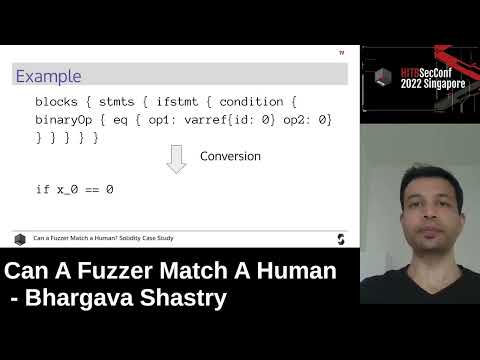
Can A Fuzzer Match A Human
Add to list
#Conference Talks
#Hack In The Box Security Conference
#Information Security (InfoSec)
#Cybersecurity
#Threat Modeling
#Programming
#Software Development
#Software Testing
#Fuzzing