Description:
Explore the vulnerabilities of Inter-Process Communication (IPC) in this conference talk from Hack.lu 2018. Delve into the concept of Man-in-the-Machine (MitM) attacks and examine various IPC mechanisms, including network sockets on localhost and Windows named pipes. Investigate potential security risks in standalone password managers, analyzing specific cases like RoboForm and 1Password. Learn about client and server impersonation techniques, as well as Man-in-the-Middle attacks on Password Boss. Discover the security implications for FIDO U2F keys and unauthorized access. Gain insights into mitigation strategies to address these vulnerabilities and enhance IPC security.
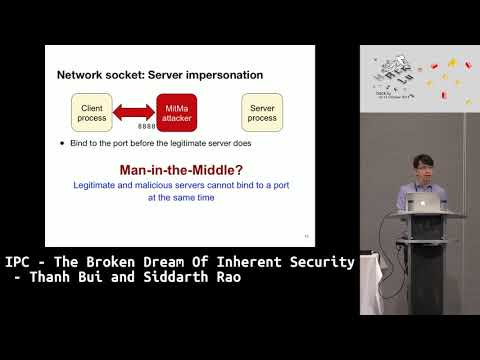
IPC - The Broken Dream of Inherent Security
Add to list
#Conference Talks
#Hack.lu
#Information Security (InfoSec)
#Cybersecurity
#Network Security
#Man in The Middle Attacks
#Password Managers