Description:
Explore a groundbreaking security research presentation that reveals how smartphone gyroscopes can be exploited for eavesdropping without microphone access. Delve into the technical details of how gyroscopes in modern smartphones are sensitive enough to capture acoustic signals, potentially allowing unauthorized apps and websites to listen in on nearby conversations. Learn about the experimental setup, speech analysis techniques, and machine learning classifiers used to demonstrate gender identification, speaker recognition, and isolated word detection using gyroscope data. Examine the implications of this vulnerability across various iOS and Android devices, and discover potential software and hardware defenses against such attacks. Gain insights into the broader security concerns surrounding sensor access in mobile devices and the importance of privacy-preserving measures in app development and web design.
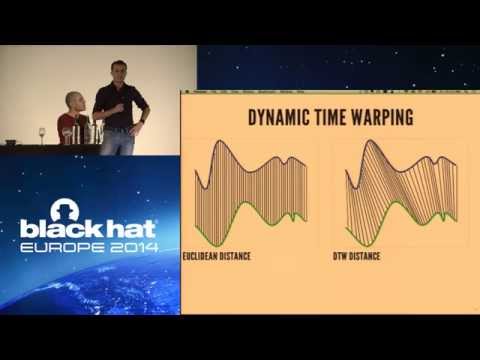
Gyrophone - Eavesdropping Using a Gyroscope
Add to list
#Conference Talks
#Black Hat
#Information Security (InfoSec)
#Cybersecurity
#Mobile Security
#Mobile Device Security
#Computer Science
#Artificial Intelligence
#Speech Analysis
#Engineering
#Electrical Engineering
#Sensors
#Gyroscope