Description:
Explore innovative approaches to enhancing data transfer security in this 42-minute conference talk from BSidesLV 2014. Delve into infrastructure considerations, high connectivity options, VPNs, and network zoning strategies. Learn about unidirectional gateways, database replication techniques, and the concept of state transfer devices. Discover how to plan and operationalize secure data transfer methods, with a focus on the science behind reliability and the Law of Sufficient Variety. Examine the benefits of simplifying processes and understand where these security measures fit within various protocols and vendor ecosystems. Gain insights into improving your organization's data transfer security posture while maintaining efficiency and effectiveness.
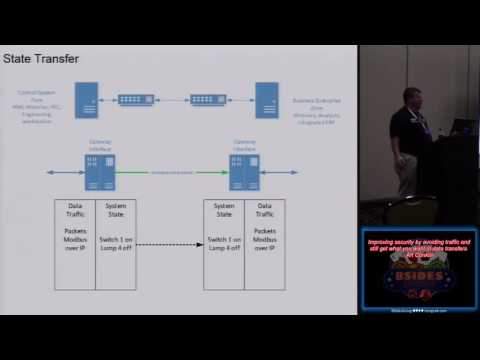
Improving Security by Avoiding Traffic and Still Get What You Want in Data Transfers
Add to list
#Conference Talks
#Security BSides
#Information Security (InfoSec)
#Network Security
#Computer Science
#Computer Networking
#VPN
#Cybersecurity
#Infrastructure Security