Description:
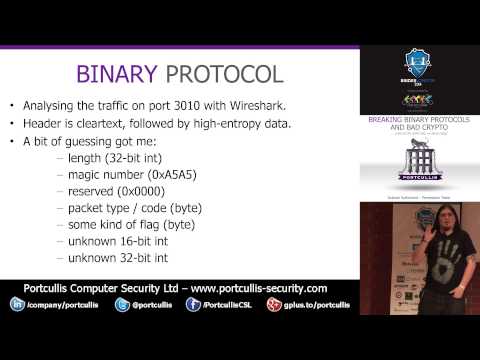
Explore the process of reverse-engineering and exploiting network devices in this 44-minute Security BSides London talk. Delve into Graham Sutherland's journey from having little knowledge of a widely deployed system to developing powerful exploits. Learn techniques for analyzing and attacking binary protocols, including a method for classifying and identifying unknown cryptography. Gain insights into the initial approach, reverse engineering process, and crypto classification. Discover how to analyze traffic, payloads, and packet structures. Understand the importance of differential cryptanalysis and packet encryption. Follow along as Sutherland shares his experiences with SSL, Diffie-Hellman, and HTTP encryption. Perfect for security professionals and enthusiasts looking to enhance their skills in breaking binary protocols and bad crypto.
Breaking Binary Protocols and Bad Crypto
Add to list
#Conference Talks
#Security BSides
#Information Security (InfoSec)
#Cybersecurity
#Computer Science
#Cryptography
#Network Security
#Reverse Engineering
#Network Traffic Analysis
#Cryptanalysis
#Differential Cryptanalysis