Description:
Explore the evolution from selective to adaptive security in functional encryption schemes through this informative conference talk. Delve into the formalization, literature review, and key theorems surrounding this cryptographic concept. Examine the bootstrapping theorem, adaptive functional encryption, and hybrid encryption techniques. Analyze the security proof, minimum requirements, and intermediate reductions. Gain insights into the Trojan method, function keys, and the final construction. Conclude with a comprehensive summary of the advancements in functional encryption security.
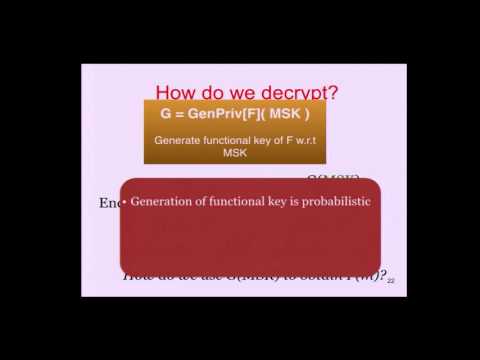
From Selective to Adaptive Security in Functional Encryption
Add to list
#Conference Talks
#Computer Science
#Cryptography
#Functional Encryption
#Information Security (InfoSec)
#Cybersecurity
#Adaptive Security