Description:
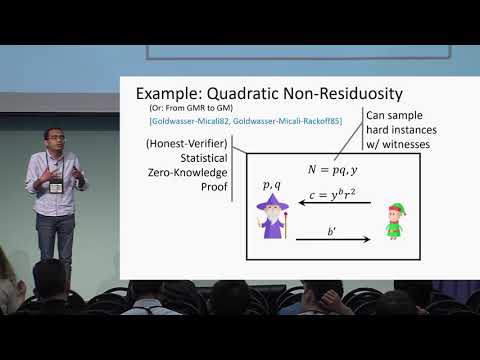
Explore a comprehensive presentation from Crypto 2018 on the connection between laconic zero-knowledge proofs and public key cryptography. Delve into topics such as Public Key Encryption (PKE), Honest-Verifier Statistical Zero Knowledge, and Quadratic Non-Residuosity. Learn about the sufficiency of certain properties, instantiations, and the relaxation of assumptions. Examine the characterization of these concepts, and investigate weak key agreement and security claims. Gain insights into coping with randomized provers and understand the progression from 2-message deterministic provers to more complex scenarios.
From Laconic Zero Knowledge to Public Key Cryptography
Add to list