Description:
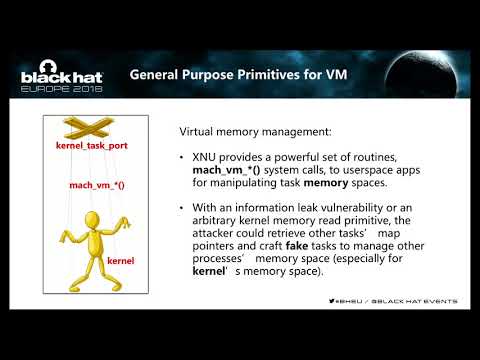
Explore a systematic assessment of Apple's recent mitigation strategies and their vulnerabilities in this Black Hat conference talk. Delve into the concept of ipc_port Kernel Object-Oriented Programming (PKOOP) and its potential for bypassing defenses through corrupting unsafe kernel objects. Examine realistic attack scenarios that can achieve full control of the latest XNU version. Learn about Apple devices, jailbreaking, and various mitigation techniques such as DEP/KASLR and Freelist Randomization. Investigate new targets like Mach Port in User Space and Struct ipc port in Kernel Space. Discover general-purpose primitives for Host and VM, as well as querying, memory interoperation, and arbitrary code execution primitives. Study practical case studies, including Yalu Exp and iOS 11 Kernel Task Mitigation. Gain insights into enterprise computer security, XNU Kernel Object Protector, and inline hooking. Evaluate the findings and discuss their implications for kernel security.
Eternal War in XNU Kernel Objects
Add to list