Description:
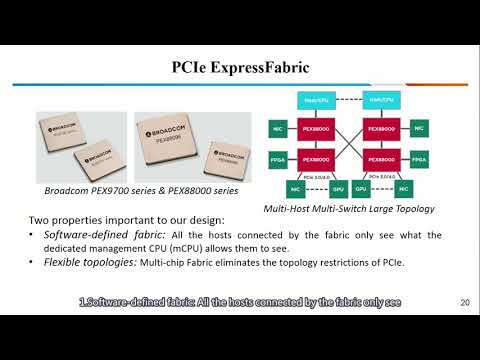
Explore a groundbreaking conference talk on enabling large-scale confidential computing through a novel Heterogeneous Trusted Execution Environment (TEE) design called HETEE. Discover how this innovative approach addresses the limitations of current TEEs by supporting high-throughput accelerators like GPUs, FPGAs, and TPUs without requiring chip-level changes. Learn about HETEE's unique architecture, which utilizes PCIe ExpressFabric for dynamic resource allocation and strong isolation, and its implementation of a thin TCB stack for security management. Gain insights into the system's performance evaluation using popular neural network inference and training tasks, showcasing minimal throughput overhead. Delve into the technical details of HETEE's components, including its security controller, hardware encryption, and remote attestation mechanisms, as well as its defense strategies against physical attacks.
Enabling Rack-Scale Confidential Computing Using Heterogeneous Trusted Execution Environment
Add to list
#Programming
#Cloud Computing
#Confidential Computing
#Information Security (InfoSec)
#Cybersecurity
#Computer Security
#Hardware Security
#Threat Modeling