Description:
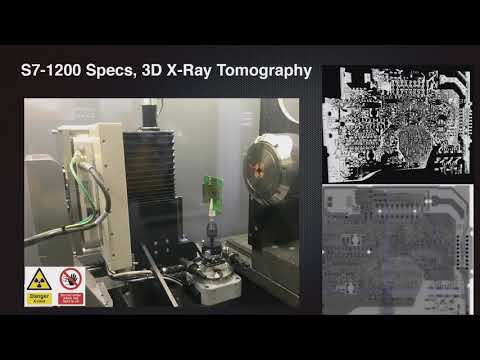
Explore a comprehensive analysis of the security measures in Siemens S7 PLC series, focusing on firmware integrity verification and bootloader code. Delve into the intricate details of industrial automation components, examining recent attacks against Industrial Control Systems (ICS) and the S7-1200 V4 PLC hardware. Investigate the S7-1200 v4 architecture, including its SOC decapsulation, embedded memory, and 3D X-Ray tomography. Gain insights into Siemens firmware components, execution mode stack, and ADONIS MPU configuration. Understand the firmware boot process, update procedures, and undocumented HTTP handlers. Discover the special access features and primary handlers after handshake. Analyze the x80 handler, update mode function, and 0x1C primary handler. Learn about the Siemens S7-1200 PLC bootloader arbitrary code execution vulnerability. Conclude with future implications and potential areas for further research in industrial automation security.
Doors of Durin - The Veiled Gate to Siemens S7 Silicon
Add to list
#Conference Talks
#Black Hat
#Business
#Finance
#Stock Trading
#Technical Analysis
#Engineering
#Manufacturing
#Industrial Automation
#Electrical Engineering
#Embedded Systems
#Firmware Analysis