Description:
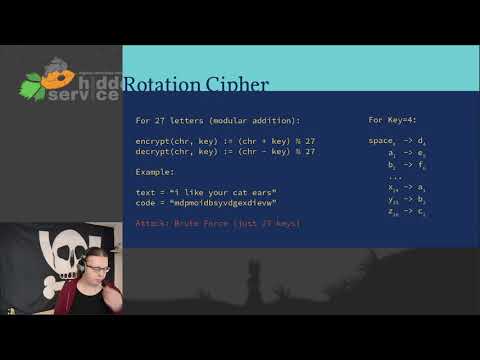
Explore quantum hardening in cryptographic protocols through this 51-minute conference talk. Gain insights into the potential impact of practical quantum computers on existing cryptographic systems and learn when to start addressing these concerns. Delve into the design of modern cryptographic protocols, with an option to skip to the quantum hardening section at the 29-minute mark. Cover topics such as ancient cryptography, block ciphers, authentication tags, key derivation, asymmetric cryptography, Diffie-Hellman key exchange, Grover's and Shor's algorithms, current quantum computer capabilities, key encapsulation, digital signatures, robust combiners, and implementations of symmetric cryptography. Access additional resources, including blog posts and a German version of the talk, to further enhance your understanding of quantum hardening in cryptography.
Quantum Hardening Cryptographic Protocols - DiVOC - 2020
Add to list
#Conference Talks
#Information Security (InfoSec)
#Cybersecurity
#Computer Science
#Cryptography
#Quantum Computing
#Grover's Algorithm
#Shor's Algorithm