Description:
Explore an in-depth analysis of person re-identification techniques in this 23-minute lecture from the University of Central Florida. Delve into various network architectures, including Triplet Loss, Quadruplet Loss, and Diffusion-based approaches. Learn about the innovative Deep Constrained Dominant Sets (DCDS) method and its implementation in person re-identification tasks. Understand the concept of Dominant Sets Clustering and its constrained variant. Discover the role of Auxiliary Networks and the process of Constraint Expansion in improving re-identification accuracy. Examine the pipeline of DCDS-based networks and evaluate their performance through comprehensive results.
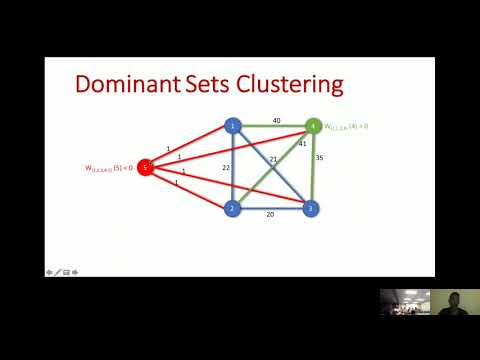
Deep Constrained Dominant Sets for Person Re-Identification
Add to list
#Computer Science
#Artificial Intelligence
#Computer Vision
#Machine Learning
#Deep Learning
#Neural Networks
#Image Processing
#Pattern Recognition
#Biometrics