Description:
Explore credential attack reconnaissance detection techniques and learn how to reduce false positives in User and Entity Behavior Analytics (UEBA) and Network Intrusion Detection (NID) tools. Discover the current limitations of these security tools and their filtering methods. Gain insights into effective strategies for identifying potential attackers, such as monitoring nonsense word usage, flagging standard password list compilations, and detecting rapid requests on webpages with unencrypted user IDs. Learn to establish baselines for normal versus suspicious behaviors, recognize sequential patterns in login attempts, and implement measures to thwart attacker persistence. Enhance your organization's security posture by understanding and applying these advanced detection methods to protect against credential-based attacks.
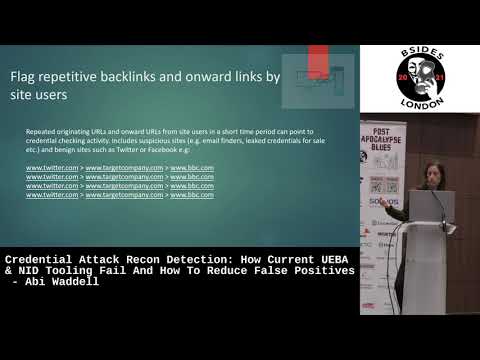
Credential Attack Recon Detection - How Tooling Fail and How to Reduce False Positives
Add to list
#Conference Talks
#Security BSides
#Information Security (InfoSec)
#Cybersecurity
#Business
#Marketing
#Digital Marketing
#Web Analytics
#User Behavior Analysis