Description:
Explore a comprehensive talk on co-design and co-verification of masked software implementations on CPUs. Delve into physical side-channel attacks, the hardware/software gap, and the co-verification flow of Coco. Examine software constraints for register files, evaluate solutions to various problems, and gain insights into future developments in this field. Learn from Barbara Gigerl's expertise as she presents at TASER 2021, offering valuable knowledge for those interested in secure software implementation and CPU architecture.
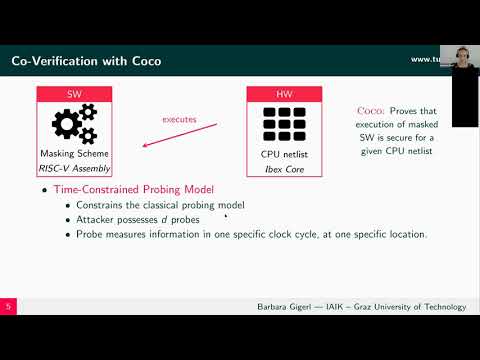
Co-Design and Co-Verification of Masked Software Implementations on CPUs
Add to list
#Computer Science
#Computer Architecture
#CPU Architecture
#Cryptography
#Information Security (InfoSec)
#Cybersecurity
#Software Security
#Side Channel Attacks
#Business
#Design Thinking
#Co-Design