Description:
Explore the intricacies of obtaining permission for penetration testing in this 43-minute conference talk from BSides Philly 2016. Delve into the challenges of securing approval, addressing client needs, and navigating legal issues in cybersecurity testing. Learn about defining scope, avoiding pitfalls with external devices, and handling potential catastrophic failures. Gain insights on determining allowed actions, measuring success, and recognizing definite failures in penetration testing scenarios. Conclude with a call to action and engage in a Q&A session to deepen your understanding of ethical hacking practices.
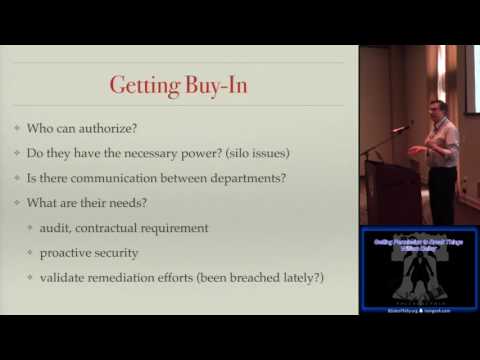
Getting Permission to Break Things
Add to list
#Conference Talks
#Information Security (InfoSec)
#Cybersecurity
#Ethical Hacking
#Business
#Project Management
#Stakeholder Management
#Programming
#Software Development
#Software Testing
#Security Testing