Description:
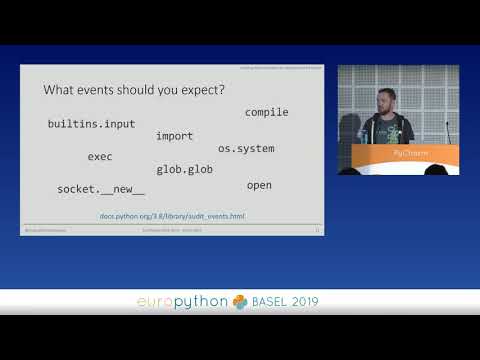
Explore the implementation of security transparency and auditing hooks in CPython with this EuroPython 2019 conference talk. Delve into the motivations behind Python Enhancement Proposals 551 and 578, which aim to detect and prevent anomalous or malicious use of Python. Learn about the concept of auditing hooks and verified open calls for reading code from files, set to be introduced in Python 3.8. Discover how these security enhancements can be integrated with Linux and Windows security frameworks to improve threat detection and prevention. Gain insights into the potential scope, limitations, and future implications of these security measures for the Python community. Examine practical examples, implementation details, and open issues surrounding this initiative to create a more secure Python interpreter while maintaining its usefulness for developers.
Auditing Hooks and Security Transparency for CPython
Add to list
#Conference Talks
#EuroPython
#Information Security (InfoSec)
#Cybersecurity
#Computer Security
#Security Engineering
#Programming
#Programming Languages
#Python
#CPython