Description:
Explore the legal landscape of bug bounty programs in this 25-minute conference talk from BSidesLV 2017. Delve into the complexities of legal terms, safe harbors, and implications for hackers and companies. Examine real-world examples from Alibaba, Facebook, and Microsoft to understand the paradoxes and risks involved. Learn about the importance of platforms, participation restrictions, and intermediaries in shaping bug bounty ecosystems. Discover suggestions for improving legal frameworks, including eliminating reverse engineering language, standardizing terms, and providing specific authorization. Gain insights into the intersection of law and cybersecurity, and understand the call for action to create more equitable and effective bug bounty programs.
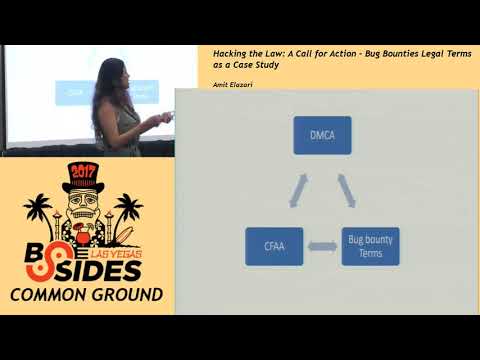
Hacking the Law - A Call for Action – Bug Bounties Legal Terms as a Case Study
Add to list
#Conference Talks
#Security BSides
#Information Security (InfoSec)
#Cybersecurity
#Social Sciences
#Law
#Technology Law