Description:
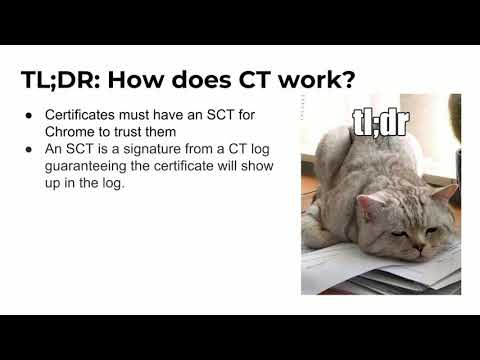
Explore the world of Certificate Transparency (CT) logs in this 33-minute conference talk from BSidesSF 2019. Dive deep into the mechanics of CT logs, their role in web security, and their potential for misuse. Learn how these append-only logs bring auditability and accountability to the public web certificate ecosystem. Discover the importance of CT logging in modern browsers like Chrome and its impact on the web's ecosystem. Investigate novel and potentially nefarious uses of CT logs, including their unexpected role as a repository for cat pictures. Gain insights into the structure of CT logs, Signed Certificate Timestamps (SCTs), and how they can be exploited. Through examples and demonstrations, understand concepts like public keys, persistent data storage, chunking, and cataloging in the context of CT logs. Conclude with a discussion on entropy, multi-domain certificates, and final thoughts on the implications of this technology for internet security and unexpected uses.
Cats in My Certificate Transparency Logs
Add to list
#Conference Talks
#Security BSides
#Information Security (InfoSec)
#Cybersecurity
#Web Security
#Computer Science
#Information Technology
#Data Management
#Data Integrity
#Cryptography
#Public Key Infrastructure
#Certificate Transparency