Description:
Explore the evolution of honeypots and dynamic deception techniques in enterprise network defense through this BSidesSF 2018 conference talk. Delve into the concept of "Honeypots 2.0" and learn how modern technologies like virtualization, cloud computing, containers, and DevOps tool chains enable scaling honeypots for greater impact in large-scale enterprise networks. Discover the potential of the Python-based Twisted networking framework for developing advanced honeypot technologies. Gain insights into honeypot essentials, scaling strategies, and the implementation of dynamic deception at scale. Examine practical examples, including Modbus and dynamic implementations, with less than 20 lines of code. Understand the relevance of these techniques in defending against insider threats and securing Industrial Internet of Things (IIoT) environments.
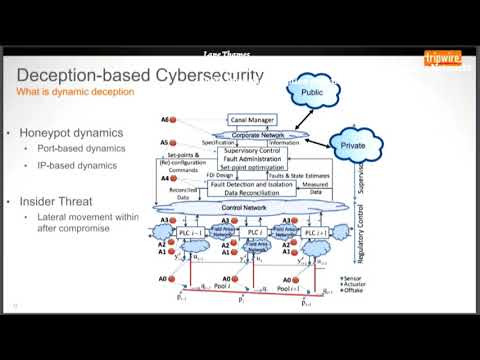
Honeypots 2.0 - A New Twist on Defending Enterprise Networks
Add to list
#Conference Talks
#Security BSides
#Information Security (InfoSec)
#Cybersecurity
#Programming
#Programming Languages
#Python
#Honeypots
#Insider Threats