Description:
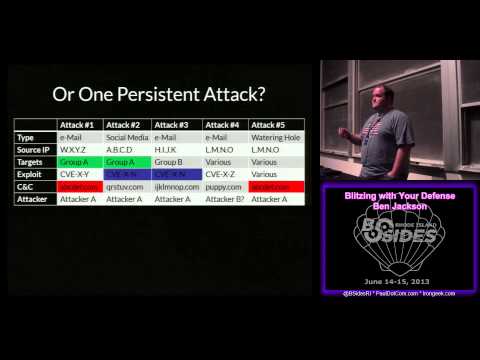
Explore incident response strategies and active defense techniques in this conference talk from BSides Rhode Island. Dive into the Incident Response Model and compare it with the adversary's approach using the Intrusion Kill Chain. Learn how to transform data into actionable intelligence and distinguish between multiple attacks versus a single persistent threat. Gain insights on developing believable intelligence and understanding the role of informal communities in cybersecurity. Discover what active defense truly entails, its benefits, and how it can delay attackers. Watch a live demonstration and engage with the speaker's concluding thoughts on effective cybersecurity practices.
Blitzing with Your Defense - Active Incident Response Strategies
Add to list
#Information Security (InfoSec)
#Cybersecurity
#Incident Response
#Network Security
#Threat Intelligence
#Cyber Attacks
#Active Defense