Description:
Explore innovative hacking techniques using light and sound in this BruCON Security Conference talk. Discover how to leverage off-the-shelf hardware for C2 channels, exfiltration, and surveillance, bypassing traditional security protections. Learn about light-based and near-ultrasonic sound attacks, disabling motion detectors, laser microphones, and even catapulting drones. Gain insights into real-world case studies, advantages and disadvantages of these methods, and potential future developments. Understand how these techniques work and their practical applications in penetration testing. Explore mitigation strategies for defenders to counter these novel attack vectors. Dive into topics such as ambient light sensors, air gap breaches, infrared signal manipulation, and delayed auditory feedback. Conclude with a summary of pros and cons, mitigations, and future research directions in this cutting-edge area of cybersecurity.
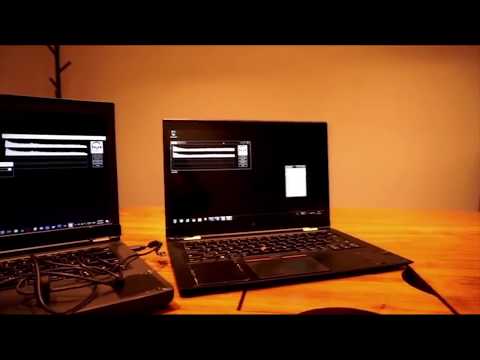
Hacking Invisibly and Silently with Light and Sound
Add to list
#Conference Talks
#BruCON
#Information Security (InfoSec)
#Cybersecurity
#Network Security
#Ethical Hacking
#Data Exfiltration
#Hardware Hacking