Description:
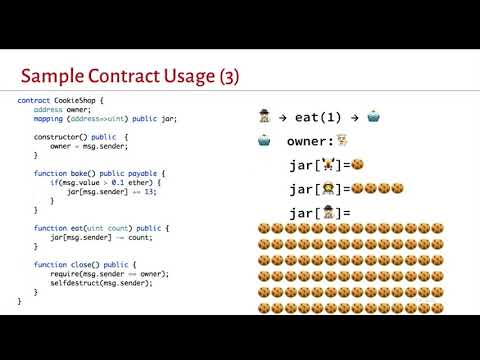
Explore Ethereum smart contract vulnerabilities and attack analysis in this 39-minute Black Hat conference talk. Dive into the world of blockchain security as Jay Little introduces Ethereum smart contracts, demonstrates reverse engineering techniques for binary-only contracts, and highlights common vulnerability classes. Learn to investigate attacks on contracts using new tools that re-process blockchain ledger data, recreate contracts with state, and analyze suspect transactions through traces and heuristics. Gain insights into Ethereum implementation, EVM (Ethereum Virtual Machine), Solidity behaviors, and issues like uninitialized variables. Discover tools such as Ethersplay, IDA-EVM, Mythril, and Manticore for smart contract analysis. Explore blockchain data, web3.js and web3.py libraries, and techniques for finding contracts. Examine real-world examples of contract creations, deaths, and massive self-destructs. Enhance your understanding of blockchain security and smart contract vulnerabilities to better protect and analyze Ethereum-based systems.
Read more
Blockchain Autopsies - Analyzing Ethereum Smart Contract Deaths
Add to list
#Conference Talks
#Black Hat
#Information Security (InfoSec)
#Reverse Engineering
#Programming
#Programming Languages
#Solidity
#Computer Science
#Blockchain Development
#Blockchain Security
#Cybersecurity
#Vulnerability Analysis