Description:
Explore social engineering techniques to improve organizational security acceptance in this Black Hat USA 2012 conference talk. Discover how to bridge the gap between information security teams and users, enhancing security awareness and policy adherence. Learn to overcome departmental conflicts, communicate effectively with non-technical management, and apply social engineering tactics to blend in and understand user perspectives. Gain insights on adapting security plans based on user feedback, championing information security within the organization, and balancing business needs with security requirements. Examine a case study on proximity card login and develop strategies to transform information security from an obstacle into an integral part of organizational culture.
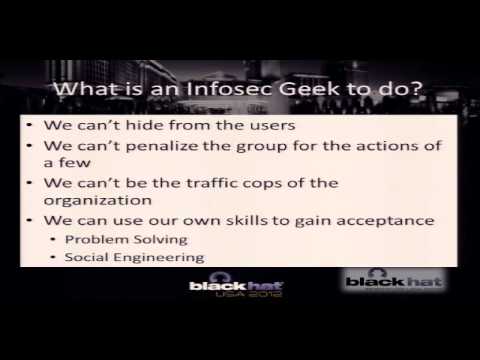
Hacking the Corporate Mind - Using Social Engineering to Improve Organizational Security Acceptance
Add to list
#Conference Talks
#Black Hat
#Information Security (InfoSec)
#Ethical Hacking
#Social Engineering
#Cybersecurity
#Security Awareness
#Organizational Security