Description:
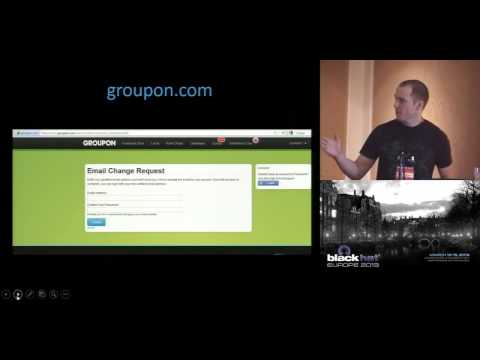
Explore the complexities and pitfalls of the same origin policy in this Black Hat EU 2013 conference talk. Delve into practical examples of attacks occurring between browser tabs, examining scenarios where common content-isolation mechanisms fail to protect against CSRF, clickjacking, and NTLM attacks. Learn about the challenges in completely mitigating these vulnerabilities, including cookie scope issues, framework weaknesses, and single sign-on complications. Discover practical CSRF tips, unconventional attack ideas, and strategies for improving web application security. Gain insights into OAuth2 vulnerabilities, browser manipulation techniques, and the importance of thorough security implementation in web frameworks.
The Deputies Are Still Confused
Add to list
#Conference Talks
#Black Hat
#Information Security (InfoSec)
#Ethical Hacking
#Clickjacking
#Cybersecurity
#Web Security
#Same-Origin Policy