Description:
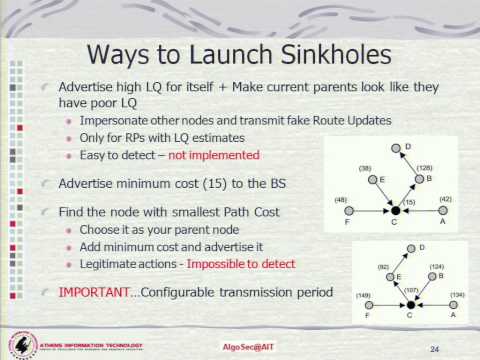
Explore a comprehensive tool for penetrating and analyzing wireless sensor networks in this Black Hat EU 2010 conference talk. Delve into the vulnerabilities of autonomous sensor devices and learn how attackers can exploit their limited resources to gain unauthorized access. Discover the tool's capabilities for passive monitoring of transactional data and executing various attacks against sensor networks. Examine its flexibility in application across different sensor network operating systems and protocol stacks. Gain insights into potential weaknesses in security protocols and understand how this tool can be used proactively to enhance network security. Follow along as the speaker covers topics such as wireless sensors, sensor platforms, stored program images, network sniffing, data replay attacks, sinkhole attacks, selective forwarding, and program image dissemination.
Weaponizing Wireless Networks - Attack Tool for Attacks against Sensor Networks
Add to list
#Conference Talks
#Black Hat
#Information Security (InfoSec)
#Cybersecurity
#Computer Science
#Internet of Things
#Sensor Networks
#Wireless Networks