Description:
Explore the vulnerabilities in ECDSA signatures and their real-world implications in this 45-minute presentation from the Workshop on Attacks in Cryptography 2 (WAC2). Delve into lattice attacks, cryptanalysis techniques, and the consequences of weak implementations. Examine case studies including the Dark Wallet compromise and random number generation vulnerabilities. Investigate countermeasures, implicit assumptions, and the fragility of cryptographic systems under human error. Gain insights into memory-unsafe code, shared 32-bit signatures, and other critical issues affecting cryptographic security in practice.
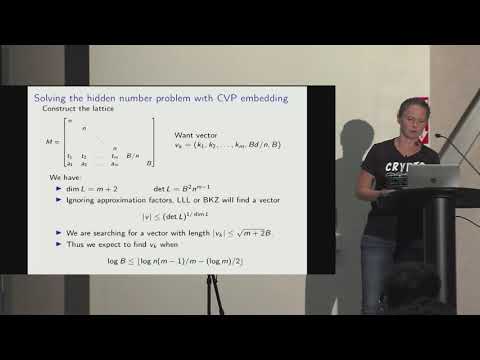
Biased Nonce Sense - Lattice Attacks Against Weak ECDSA Signatures in the Wild
Add to list