Description:
Explore the hidden behaviors in mobile apps through an analysis of input validation techniques. Learn how to uncover undisclosed functionalities like backdoors and blacklists using INPUTSCOPE, an automated tool designed to detect execution contexts and content involved in user input validation. Discover the findings from a comprehensive study of over 150,000 mobile apps, including popular and pre-installed applications, revealing thousands of apps with hidden backdoor secrets and blacklist content. Gain insights into the detailed design of INPUTSCOPE, including input validation detection, content resolution, context recovery, and secret uncovering. Examine experiment results across various secret types such as access keys, master passwords, secret commands, and blacklists. Discuss the implications of these findings and related work in the field of mobile app security.
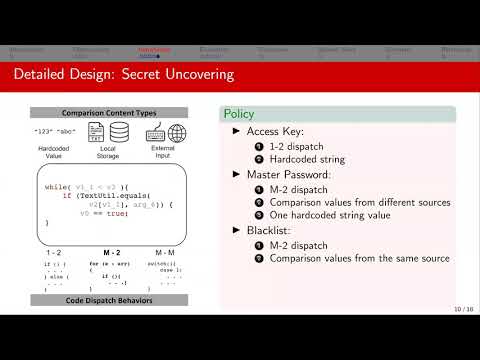
Automatic Uncovering of Hidden Behaviors from Input Validation in Mobile Apps
Add to list
#Programming
#Web Development
#Input Validation
#Software Development
#Information Security (InfoSec)
#Cybersecurity