Description:
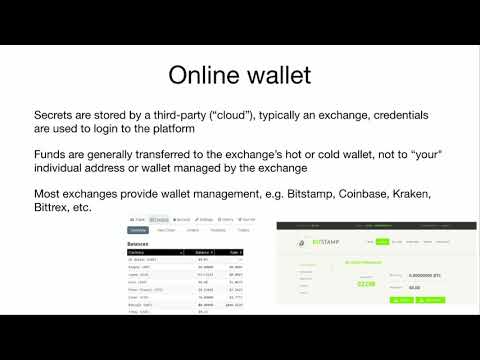
Explore a comprehensive conference talk that delves into the world of blockchain security, examining notorious failures and providing strategies for risk mitigation. Analyze dramatic Ethereum smart contract issues, objectively evaluate the case of Iota's custom crypto, and discover how millions of dollars worth of tokens could have been stolen. Gain insights into bugs found in popular Bitcoin software utilities and learn about various types of crypto wallets, including hot wallets, online wallets, mobile wallets, desktop wallets, paper wallets, and hardware wallets. Understand the advantages and disadvantages of each wallet type, and discover best practices for securing your digital assets. Examine the design and implementation of Bitcoin, explore the worst bugs in blockchain history, and learn about smart contract attacks and programming. Dive into the ethics of blockchain security, double spend attacks, and design bugs. Conclude with a discussion on the importance of proper cryptography design and the challenges faced in the blockchain industry.
Read more
Attacking and Defending Blockchains - From Horror Stories to Secure Wallets
Add to list
#Conference Talks
#Black Hat
#Business
#Finance
#Fintech
#Cryptocurrency
#Computer Science
#Blockchain Development
#Blockchain Security