Description:
Explore cutting-edge developments in multiparty computation through this comprehensive conference session from Asiacrypt 2022. Delve into topics such as protocol motivation, obvious transfer, interactive key exchange, and biometric authentication. Examine the intricacies of primal form, malicious security, and Byzantine key properties. Gain insights into player replaceability, multiplicative overhead, and the state-of-the-art VA Protocol. Enhance your understanding of complex cryptographic concepts and their practical applications in secure multiparty computations.
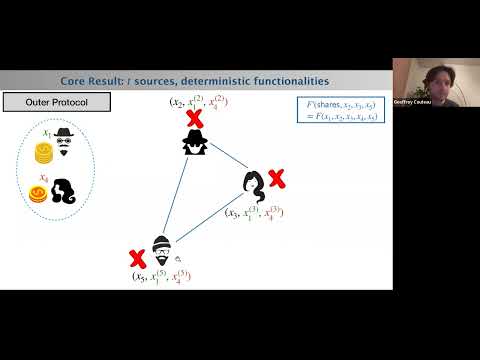
Multiparty Computation Protocols - Session 1
Add to list
#Computer Science
#Cryptography
#Information Security (InfoSec)
#Cybersecurity
#Biometric Authentication