Description:
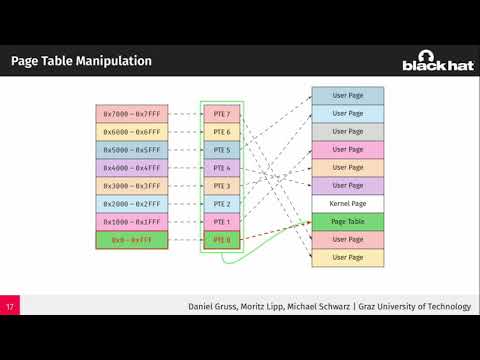
Explore the Rowhammer bug, a critical vulnerability in DRAM modules, through this 50-minute Black Hat conference talk. Delve into the mechanics of DRAM reading, timing differences, and the widespread nature of this issue. Learn about access techniques, physical addresses, and exploitation strategies, including modifying instructions and manipulating page tables. Examine post-Rowhammer exploitation methods, such as bit flips combined with page deduplication. Investigate various mitigation techniques, including hardware and software prevention methods, as well as detection strategies. Gain insights into different hammering techniques like single-sided, double-sided, and one-location hammering. Explore advanced topics such as opcode flipping, memory waylaying, and SGX encrypted memory exploitation. Compare performance numbers and understand the implications of Nethammer bit flips in this comprehensive exploration of DRAM security vulnerabilities.
Another Flip in the Row
Add to list
#Conference Talks
#Black Hat
#Information Security (InfoSec)
#Cybersecurity
#Computer Science
#Computer Architecture
#Data Science
#Data Manipulation
#System Security