Description:
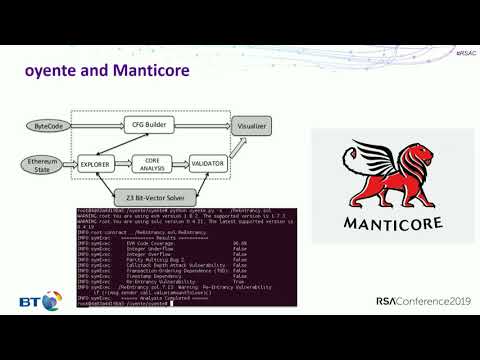
Dive into advanced Solidity hacking techniques in this 35-minute RSA Conference talk. Explore bleeding-edge exploits and learn the crucial skill of writing contracts to hack other contracts. Gain insights into the persistent security challenges in blockchain technology and understand the potential dangers of new tool advancements. Examine real-world examples like the DAO hack and Parity wallet vulnerabilities. Discover methodologies for identifying and exploiting smart contract weaknesses, including reentrancy attacks, public visibility issues, and overflow vulnerabilities. Learn about gas limits, transaction-ordering dependence, and call-stack depth limitations. Prepare for future blockchain security challenges and explore real-time protection strategies. Suitable for those with blockchain and Solidity basics, this talk equips you with advanced knowledge to enhance your smart contract hacking skills.
Advanced Smart Contract Hacking
Add to list
#Conference Talks
#RSA Conference
#Information Security (InfoSec)
#Ethical Hacking
#Business
#Finance
#Fintech
#Cryptocurrency
#Programming
#Programming Languages
#Solidity