Description:
Explore a groundbreaking approach to hypervisor security in this 17-minute IEEE conference talk. Delve into the root causes of speculative vulnerabilities and learn how to rethink hypervisor isolation through a secret-free design. Discover the allow-list approach and how hypervisors can maintain secret isolation. Examine the challenges faced and evaluate the performance of Secret-Free Xen. Gain valuable insights on protecting against unknown attacks and understand the implications for future hypervisor designs in the age of speculative vulnerabilities.
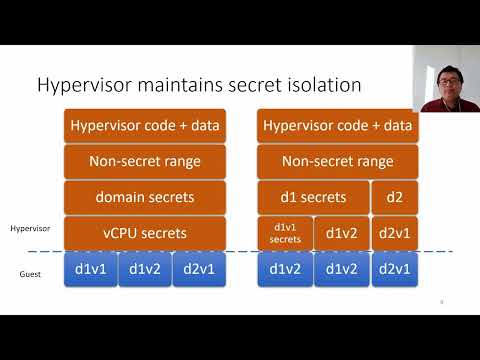
A Secret-Free Hypervisor - Rethinking Isolation in the Age of Speculative Vulnerabilities
Add to list