Description:
Explore a comprehensive retrospective on five years of IoT vulnerability research and numerous zero-day exploits presented at DefCamp 2021. Delve into topics such as reusable attack vectors, authentication packets, cloud implementations, command injection, MQTT and RSTP leaks, buffer overflow, and cloud-related attacks. Gain insights on vulnerability tracking, policy changes, and strategies for avoiding high-profile brands in IoT security research. Learn from hands-on experiences and practical approaches to identifying and addressing security vulnerabilities in the rapidly evolving Internet of Things landscape.
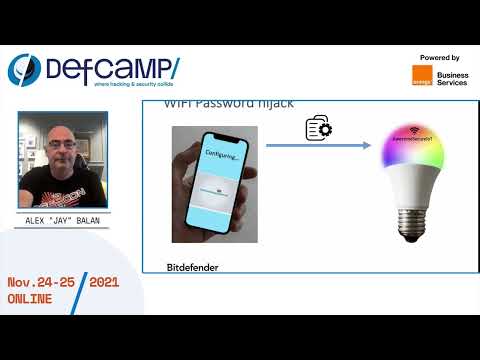
Years of IoT Vulnerability Research and Countless 0days - A Retrospective - DefCamp - 2021
Add to list
#Conference Talks
#DefCamp
#Computer Science
#Internet of Things
#MQTT
#Information Security (InfoSec)
#Ethical Hacking
#Command Injection