Description:
Explore advanced network security concepts in this 57-minute conference talk from BSides Nashville 2014. Delve into topics such as router shell access, policy routing, GRE tunneling, ER Span, DLSW, IPv6 vs IPv4, L2TPv, layer 2 security, lawful intercept, DHCP snooping, OSPF, rules of engagement, BGP, physical access rules, BGP hijacking, trust relationships, monitoring prefixes, protocol tools, and router culture. Gain insights into bending and twisting networks to enhance security measures and understand potential vulnerabilities.
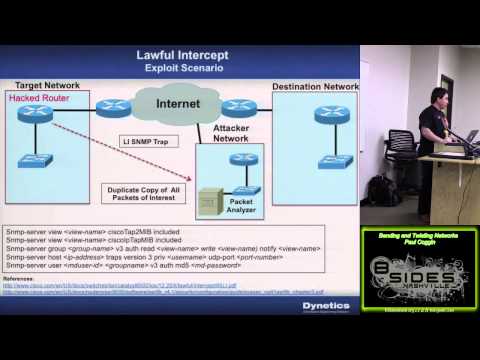
Bending and Twisting Networks: Advanced Router Techniques - Session 300
Add to list
#Information Security (InfoSec)
#Network Security
#Computer Science
#IPv6
#Information Technology
#DHCP
#Computer Networking
#Network Monitoring
#Router Configuration
#OSPF
#BGP