Description:
Explore threat detection and response strategies using Hipara in this conference talk from GrrCon 2016. Gain insights into Hipara's signature-based approach, repository management, and endpoint philosophy. Learn about Yarra implementation, commandline logging techniques, and ransomware detection methods focusing on entropy and encryption. Discover deployment strategies, web server setup, and user interface design for effective threat management. Engage with a comprehensive overview of Hipara's capabilities in cybersecurity, concluding with a Q&A session to address specific concerns and applications.
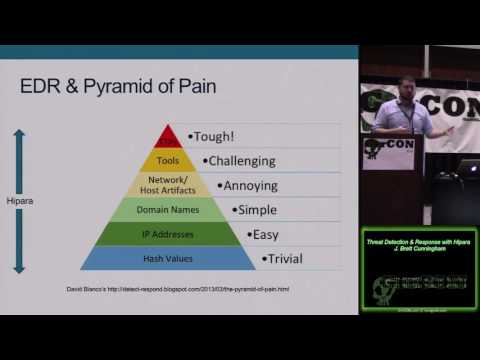
Threat Detection Response with Hipara
Add to list
#Conference Talks
#Information Security (InfoSec)
#Cybersecurity
#Social Sciences
#Sociology
#Criminology
#Cybercrime
#Ransomware
#Computer Science
#Cryptography
#Encryption
#Information Theory
#Entropy
#Endpoint Security
#Threat Detection