Description:
Explore embedded device security through a comprehensive conference talk on reversing and exploiting techniques. Delve into the software and hardware stack, covering topics such as binary analysis, firmware examination, debugging, assembly language, hardware exploration, and JTAG interfacing. Learn about FCC ID research, internal photo analysis, and crash analysis techniques. Compare MIPS, ARM, and x86 architectures, and gain hands-on experience with OpenOCD for debugging. Discover practical approaches to IoT security, including fuzzing methodologies and exploitation strategies, presented by Elvis Collado at GrrCon 2016.
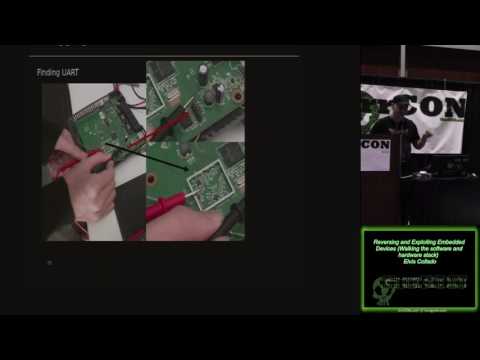
Reversing and Exploiting Embedded Devices - Walking the Software and Hardware Stack
Add to list
#Conference Talks
#Programming
#Programming Languages
#Assembly Language
#Information Security (InfoSec)
#Cybersecurity
#IoT security
#Reverse Engineering
#Binary Analysis
#Engineering
#Electrical Engineering
#Embedded Systems
#JTAG
#Firmware Analysis
#Embedded Device Security