Description:
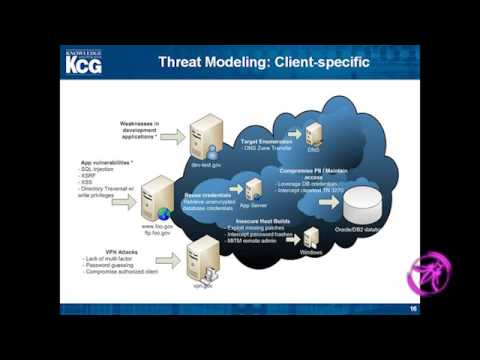
Learn how to enhance your Software Development Life Cycle (SDLC) using Common Attack Pattern Enumeration and Classification (CAPEC) and Common Weakness Enumeration (CWE) in this 35-minute conference talk by Ryan Stinson from KCG at LASCON 2012. Explore threat modeling techniques, examine CWE examples, and understand their relationships. Discover how to implement SDLC tools effectively across various stages, including requirements analysis, design considerations, development, and testing. Gain insights into application penetration testing, analyzing attack anatomy, and addressing common vulnerabilities such as input validation, error handling, SQL injection, and access control issues. Conclude with valuable lessons learned to improve your overall software security practices.
Improve Your SDLC with CAPEC and CWE
Add to list
#Conference Talks
#LASCON
#Computer Science
#Software Engineering
#Software Development Life Cycle
#Information Security (InfoSec)
#Cybersecurity
#Threat Modeling