Description:
Explore the concept of election hacking and strategies to combat it in this 49-minute conference talk from BSidesCT 2019. Delve into the origins of hacking terminology, data mining techniques, and various attack vectors using the Hexad Model. Examine real-world examples from the United Kingdom and the Netherlands, and learn about defensive techniques and potential strategies to safeguard electoral processes. Gain insights into psychometrics, physical infrastructure vulnerabilities, denial of service attacks, information-based threats, and data exfiltration risks in the context of election security.
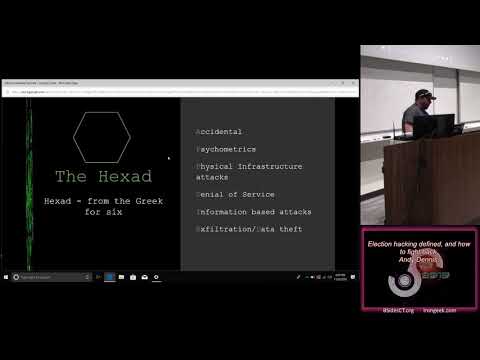
Election Hacking Defined and How to Fight Back
Add to list
#Conference Talks
#Data Science
#Data Mining
#Information Security (InfoSec)
#Cybersecurity
#Data Protection
#Denial-of-Service Attacks