Description:
Explore the intricacies of Unicode and its potential for character assassination in this comprehensive conference talk. Delve into Unicode history, encodings, and examples, including UTF-16 encoding and Mojibake. Learn about classic phishing obfuscations, homographs, and the challenges they pose to DNS. Examine browser protections, registrar defenses, and test various platforms like Outlook 2010 and Facebook. Investigate steganography techniques, name spoofing, right-to-left text manipulation, and file name vulnerabilities. Analyze non-visual attacks, canonicalization errors, and UTF-8 exploits. Discover real-life examples, such as the Spotify case, and understand how Unicode can be used to thwart searches and obscenity filters. Finally, explore the complexities of buffer overflows in relation to Unicode characters.
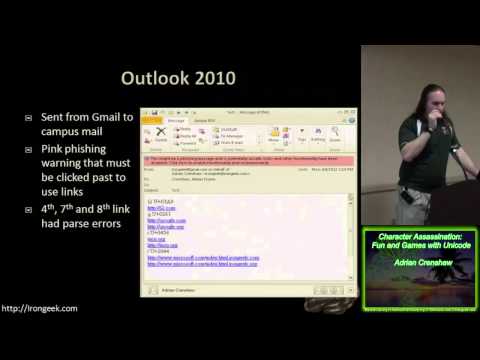
Character Assassination Fun and Games with Unicode - Adrian Crenshaw
Add to list
#Conference Talks
#Programming
#Web Development
#Information Security (InfoSec)
#Cybersecurity
#Phishing
#Computer Science
#Cryptography
#Steganography
#Unicode