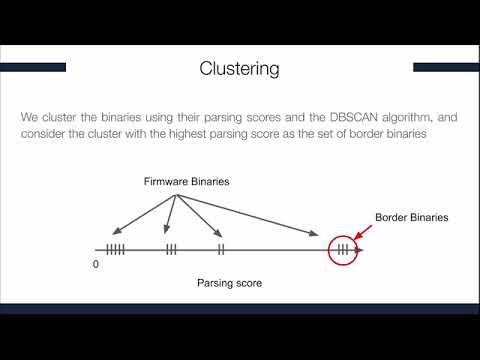
#Inter-Process Communication
YouTube
education
Showing: 28 courses

Chrome University
Welcome to Chrome University, where you will learn the foundations of how Chrome works.
Add to list
21 Lesons
9 hours
On-Demand
Free-Video
18 Lesons
16 minutes
On-Demand
Free-Video
1 Lesons
19 minutes
On-Demand
Free-Video
1 Lesons
22 minutes
On-Demand
Free-Video
1 Lesons
21 minutes
On-Demand
Free-Video
1 Lesons
28 minutes
On-Demand
Free-Video
1 Lesons
53 minutes
On-Demand
Free-Video
1 Lesons
1 hour 3 minutes
On-Demand
Free-Video
1 Lesons
1 hour 2 minutes
On-Demand
Free-Video
1 Lesons
22 minutes
On-Demand
Free-Video
14 Lesons
43 minutes
On-Demand
Free-Video
1 Lesons
47 minutes
On-Demand
Free-Video
1 Lesons
59 minutes
On-Demand
Free-Video
1 Lesons
53 minutes
On-Demand
Free-Video
31 Lesons
44 minutes
On-Demand
Free-Video
1 Lesons
43 minutes
On-Demand
Free-Video
1 Lesons
49 minutes
On-Demand
Free-Video
1 Lesons
23 minutes
On-Demand
Free-Video
26 Lesons
1 hour 4 minutes
On-Demand
Free-Video
1 Lesons
26 minutes
On-Demand
Free-Video
1 Lesons
27 minutes
On-Demand
Free-Video
12 Lesons
51 minutes
On-Demand
Free-Video
1 Lesons
44 minutes
On-Demand
Free-Video
1 Lesons
51 minutes
On-Demand
Free-Video
1 Lesons
32 minutes
On-Demand
Free-Video
1 Lesons
1 hour 1 minute
On-Demand
Free-Video
1 Lesons
39 minutes
On-Demand
Free-Video
1 Lesons
15 minutes
On-Demand
Free-Video