Description:
Discover how to secure API access using OAuth 2.0 and avoid common API security pitfalls in this 59-minute webinar. Explore various OAuth flows, including the Authorization Code Flow, and understand the intricacies of access tokens, JSON Web Tokens, and token lifetimes. Delve into different token types, browser-based applications, password grants, and Rich Authorization Requests. Learn about the importance of the state parameter and gain insights from the OAuth 2.0 Simplified book. Access additional resources, including community websites, videos, and best practices for OAuth implementation. Presented by Okta, this webinar offers valuable knowledge for developers looking to enhance API security and user account management in web and mobile applications.
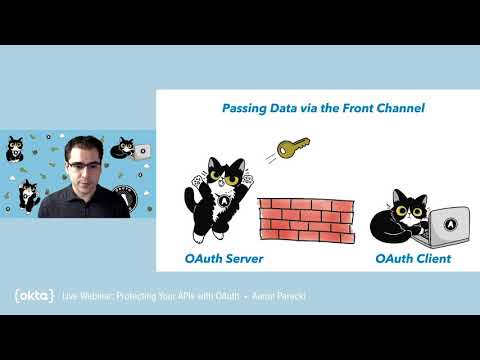
Protecting Your APIs with OAuth
Add to list
#Programming
#Web Development
#OAuth
#OAuth 2.0
#Information Security (InfoSec)
#Cybersecurity
#Web Security
#JSON Web Tokens
#API Security
#Computer Science
#Information Technology
#Access Tokens
0:00 / 0:00