Description:
Explore 10 crucial ways asset visibility strengthens operational technology (OT) cybersecurity foundations in this 45-minute webinar by Dragos experts. Gain insights into establishing "normal" baselines, verifying assets, visualizing network communications, and enhancing threat detection. Learn strategies for managing rogue assets, improving incident response, mitigating vulnerabilities, and optimizing change management. Discover how to streamline compliance reporting and justify security investments. Benefit from real-world examples and practical tips to elevate your OT cybersecurity strategy through comprehensive asset visibility.
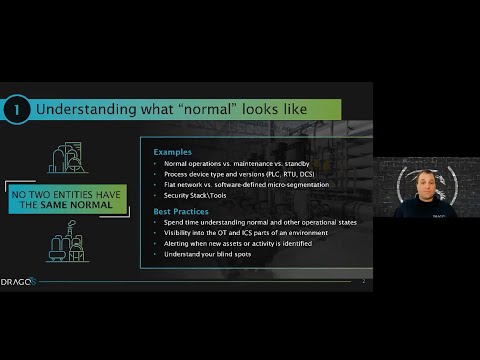
10 Ways Asset Visibility Builds an Effective OT Cybersecurity Foundation
Add to list
#Engineering
#Manufacturing
#Industrial Automation
#Industrial Control Systems
#Business
#Management & Leadership
#Change Management
#Information Security (InfoSec)
#Cybersecurity
#Incident Response
#Threat Detection
#Vulnerability Management
0:00 / 0:00