Description:
Explore a comprehensive analysis of Trusted Platform Module (TPM) vulnerabilities in this WAC 2020 presentation by Daniel Moghimi. Delve into cryptanalysis techniques, focusing on ECDSA nonce side-channel attacks and their implications for TPM security. Examine high-resolution timing tests on Intel PTT (FTPM) and understand the application of lattice-based cryptanalysis to the hidden number problem. Investigate the TPM-Fail key recovery results and their real-world impact through a case study on StrongSwan VPN. Learn about the challenges of secure cryptographic implementation, particularly for ECDSA, and discover the MicroWalk approach for identifying potential vulnerabilities. Gain valuable insights into the complexities of trusted computing and the importance of robust cryptographic implementations in modern security systems.
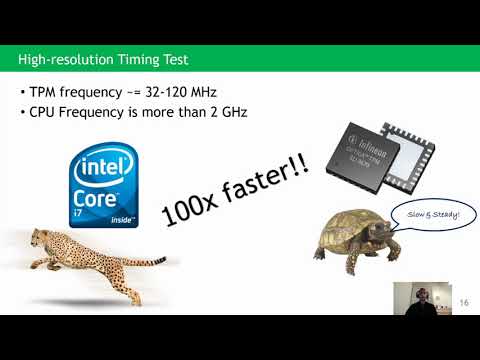
TPM-FAIL - TPM Meetings Timing and Lattice Attacks
Add to list
#Information Security (InfoSec)
#Cybersecurity
#Trusted Platform Module
#Side Channel Attacks
#Computer Science
#Cryptography
#ECDSA
#Cryptanalysis
#System Security
#Timing Attacks
0:00 / 0:00