Description:
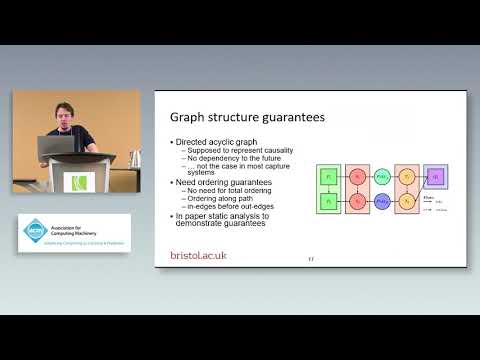
Explore runtime analysis of whole-system provenance in this 22-minute conference talk from the Association for Computing Machinery (ACM). Delve into the challenges of identifying root causes and impacts of system intrusions in real-time security applications. Examine the limitations of post-hoc analysis in provenance-based auditing techniques and discover innovative approaches to overcome these constraints. Learn about changes in provenance architecture, programming frameworks, and graph structure guarantees necessary for effective runtime analysis. Investigate various workloads, including in-kernel and userspace scenarios, through micro and macro-benchmarks. Gain valuable insights into the future of provenance-based security and its potential to revolutionize computer security practices.
Runtime Analysis of Whole-System Provenance
Add to list
#Information Security (InfoSec)
#Cybersecurity
#Intrusion Detection
#Computer Security
#Science
#Forensic Science
#Forensic Analysis
0:00 / 0:00