Description:
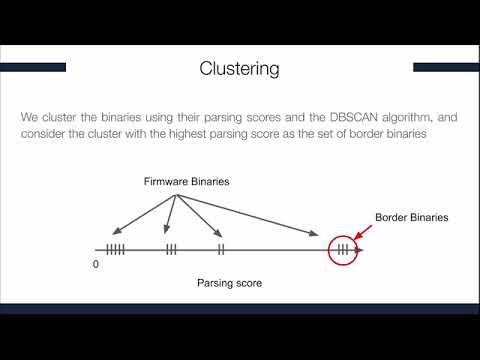
Explore KARONTE, a novel approach for detecting insecure multi-binary interactions in embedded firmware, in this 16-minute IEEE conference talk. Delve into the challenges of firmware analysis, existing single-binary analyses, and the complexities of inter-process communication. Learn about Karonte's innovative multi-binary analysis technique, including its unpacking process, border binary discovery, parsing score, clustering, and binary dependency graph algorithm. Examine the static taint engine used for insecure interaction detection and evaluate Karonte's performance in large-scale scenarios. Gain insights from researchers at the University of California, Santa Barbara and Arizona State University as they present their groundbreaking work in improving embedded device security.
KARONTE - Detecting Insecure Multi-Binary Interactions in Embedded Firmware
Add to list
#Engineering
#Electrical Engineering
#Embedded Systems
#Firmware Analysis
#Information Security (InfoSec)
#Cybersecurity
#Computer Science
#Parsing
#Machine Learning
#Clustering
#Operating Systems
#Inter-Process Communication
0:00 / 0:00