Description:
Explore the hidden dangers of USB devices in this eye-opening Black Hat conference talk. Delve into a new form of malware that operates from controller chips inside USB devices, learning how seemingly innocuous accessories can be reprogrammed to spoof other device types, compromising computer security. Witness demonstrations of full system compromise and a self-replicating USB virus that evades current defenses. Examine the USB stack to understand potential anchors for protection against USB malware. Gain insights into various attack vectors, including device identification spoofing, password exploitation, and boot sector viruses. Discover the implications for USB3 controllers, cloud environments, and GSM rainbow tables. Leave with a deeper understanding of USB security vulnerabilities and potential defense strategies.
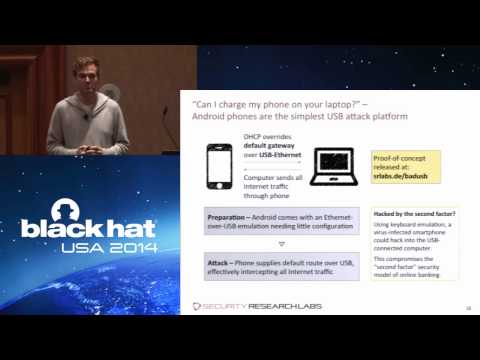
BadUSB - On Accessories that Turn Evil
Add to list
0:00 / 0:00